In the midst of heightened border tensions between India and China, researchers have uncovered a concerted campaign against India’s critical infrastructure, including the nation’s power grid, from Chinese state-sponsored groups.
The attacks coincided with the standoff between the two nations in May 2020 and targeted a total of 12 organisations, 10 of which are in the power generation and transmission sector.
The report (by Recorded Future) noted:
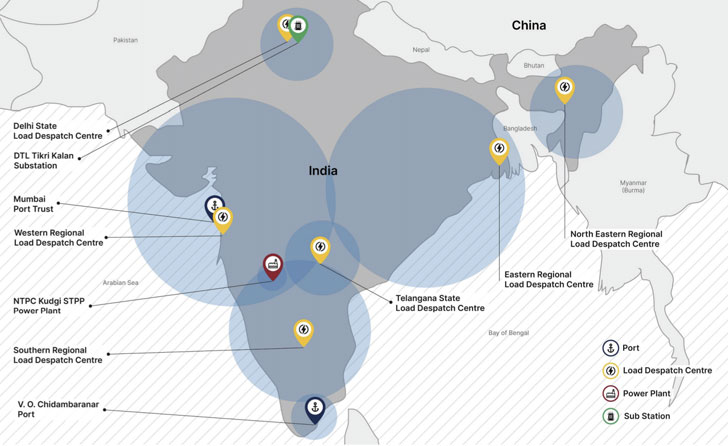
10 distinct Indian power sector organisations, including four of the five Regional Load Despatch Centres (RLDC) responsible for operation of the power grid through balancing electricity supply and demand, have been identified as targets in a concerted campaign against India’s critical infrastructure…Other targets identified included 2 Indian seaports.
China-linked Group RedEcho Targets the Indian Power Sector Amid Heightened Border Tensions by Recorded Future
Chief among the victims include a power plant run by National Thermal Power Corporation (NTPC) Limited and New Delhi-based Power System Operation Corporation Limited.
Pinning the intrusions on a new group dubbed “RedEcho,” investigators said the malware deployed by the threat actor shares strong infrastructure and victimology overlaps with other Chinese groups APT41 (aka Barium, Winnti, or Wicked Panda) and Tonto Team.
Border conflicts have flared up since last year after deadly clashes between Indian and Chinese soldiers in Ladakh’s Galwan Valley. While 20 Indian soldiers were killed in the clashes, China formally identified four casualties on its side for the first time on February 19.
In the intervening months, the Indian government banned over 200 Chinese apps for allegedly engaging in activities that posed threats to “national security and defence of India, which ultimately impinges upon the sovereignty and integrity of India.”
Noting that the standoff between the two countries was accompanied by increased espionage activity on both sides.
Additionally, the report also raises questions about a possible connection between the skirmishes and a power blackout that crippled Mumbai last October.
While initial probe conducted by the cyber department of the western Indian state of Maharashtra traced the attack to a piece of unspecified malware identified at a Padgha-based State Load Despatch Centre, the researchers said, “the alleged link between the outage and the discovery of the unspecified malware variant remains unsubstantiated.”
“However, this disclosure provides additional evidence suggesting the coordinated targeting of Indian Load Despatch Centres,” they added.
Interestingly, these cyberattacks were described as originating from Chengdu, which is also the base for a network technology firm called Chengdu 404 Network Technology Company that operated as a front for a decade-long hacking spree targeting more than 100 high-tech and online gaming companies.
But it’s not just China.
In the weeks leading to the clashes in May, a state-sponsored group called Sidewinder — which operates in support of Indian political interests — is said to have singled out Chinese military and government entities in a spear-phishing attack using lures related to COVID-19 or the territorial disputes between Nepal, Pakistan, India, and China.
The modus operandi aside, the finding is yet another reminder of how critical infrastructure continues to be a lucrative target for an adversary looking to cut off access to essential services used by millions of people.




