ISO 27001 Certification FAQs
It is possible to be compliant with ISO 27001 without an external service provider, however, having a consultant such as Gridware assist with the implementation of the ISO 270001 will ensure the process is faster and more streamline. Our ISO 27001 development program is created to meet the requirements of certification bodies, should you wish to pursue certification.
Not necessarily. To become ISO27001 certified, you require a certifying body such as SAI Global, BSI or PECB to certify that your ISMS meets the requirements of the ISO 27001. You can still create and maintain the documentation without the need to be certified.
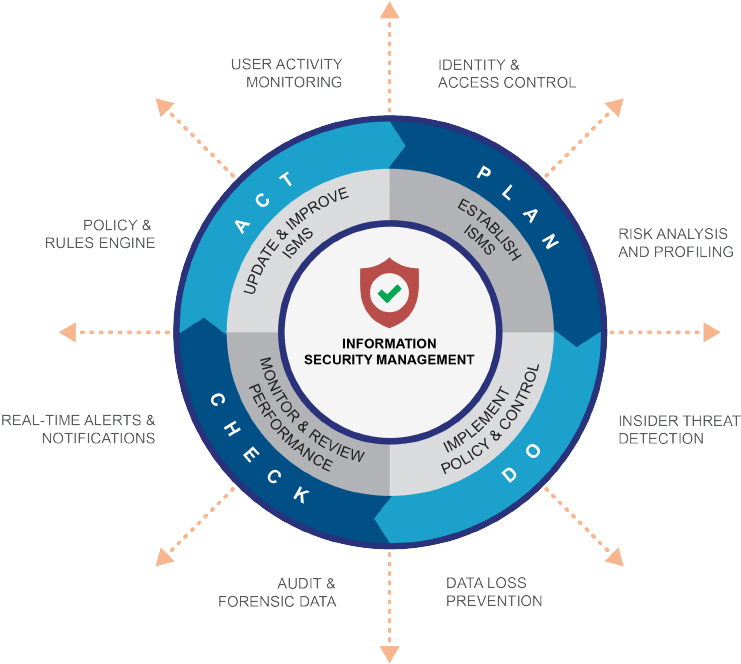
An ISMS or Information Security Management System is a set of documents, procedures and guidelines created to create a compliance framework aligned with the requirements of ISO 27001. In simple terms, it means having a set of policies, procedures and processes which align with the objectives and scope of the ISO 27001 as it is relevant to your organisation. That means it’s not just an IT policy, but also key business processes, controls, audit procedures as well as principles such as commitment by senior management for continual improvement. The full list of compliance obligations required to have an ISMS will depend on the nature, size and risk appetite of your organisation.
Not necessarily. ISMS is based on the ISO 27001 standard which relates to all aspects of information security. While some components relate to Information Technology Security Techniques, the scope of the ISO 27001 includes many other aspects such as leadership, auditing, continual improvement and management. Generally speaking, an organisations most valuable asset is information that belongs to the business. Therefore, any medium where this information is used, captured, stored or managed will fall under the scope of an ISMS.
Implementing an ISMS is a project taking into consideration all the compliance requirements of the ISO 27001, and meeting those requirements in your organisation. Clauses 4-10 of the ISO 27001 relating to the organisations context and scope, leadership and commitment, planning to address risk, support and awareness, operational planning, risk assessments, performance evaluation and continual improvement are all mandatory components of an ISMS. Once these requirements are met in the form of documentation, you should conduct a risk assessment of your information security. Relevant controls from Annexure A of the ISO can be used as guide to assist the organisation with implementing best practice controls.