Almost anyone can create a job listing on today’s leading recruitment on behalf of just about any employer. And worse, the employer can’t easily take these down.
Key takeaways
- Adding a job on behalf of a company on LinkedIn is a little too easy
- Almost anyone can add a job on behalf of anyone, including threat actors
- Experts believe this feature can be abused and could become a hotbed for phishing campaigns if LinkedIn doesn’t move to do something about it soon
Almost anyone can create a job listing on today’s leading recruitment on behalf of just about any employer. And worse, the employer can’t easily take these down.
These lax verification standards on LinkedIn pave the ways for attackers to post bogus listings for malicious purposes.
Attackers can use well honed social engineering tactics to collect personal information and resumes from professionals who believe they are applying to a legitimate company, without realising their data may be sold or used for phishing scams.
In a recent deep-dive by prominent cybersecurity website BleepingComputer, cyber expert Harman Singh discussed a feature that essentially allows “anyone to post a job under a company’s LinkedIn account and it appears exactly the same as a job advertised by a company”.
There seem to be no real blockers to an individual posting a job appearing to pass off as another organisation, and Singh demonstrated this by getting to the final stage of the process as below:
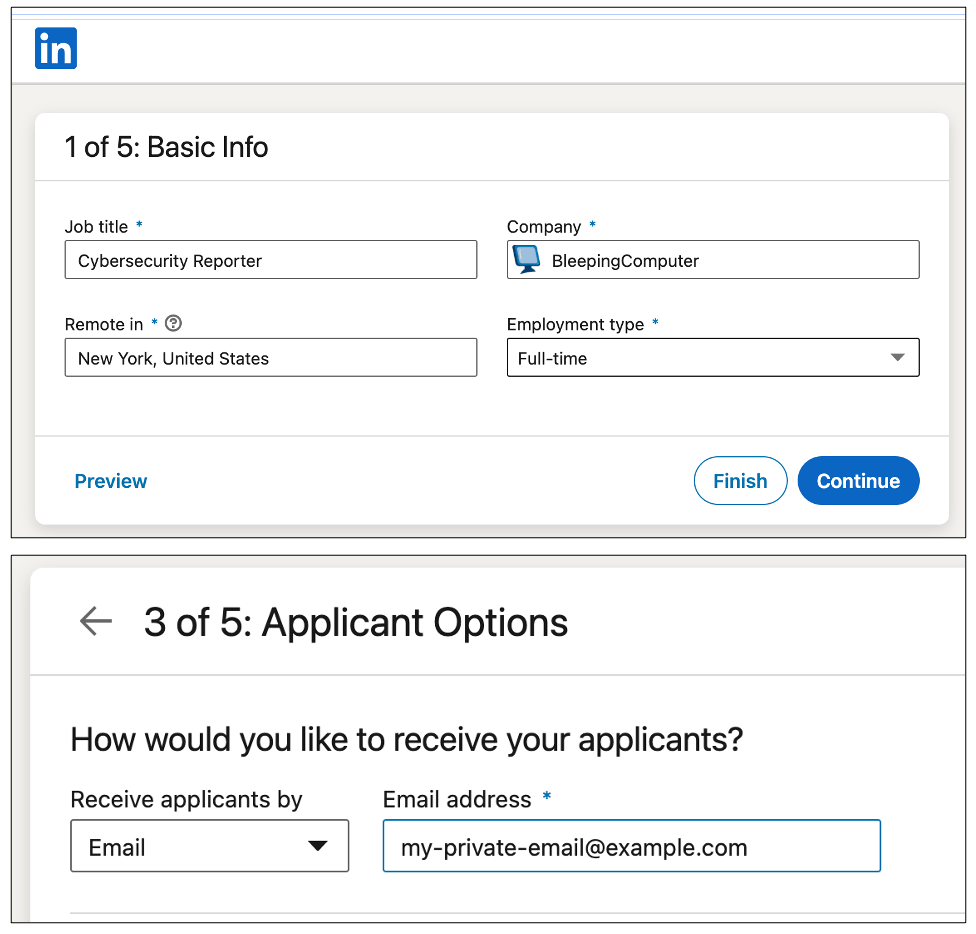
Using an unaffiliated LinkedIn account, Sing was able to successfully publish a new job posting on behalf of BleepingComputer, almost anonymously.
The job listing would appear authentic as if coming straight from BleepingComputer.
It also did not show the user account that created the posting — an option set by the user who posts the job, rather than the employer.
And, within hours of the listing going live, applications started coming in!
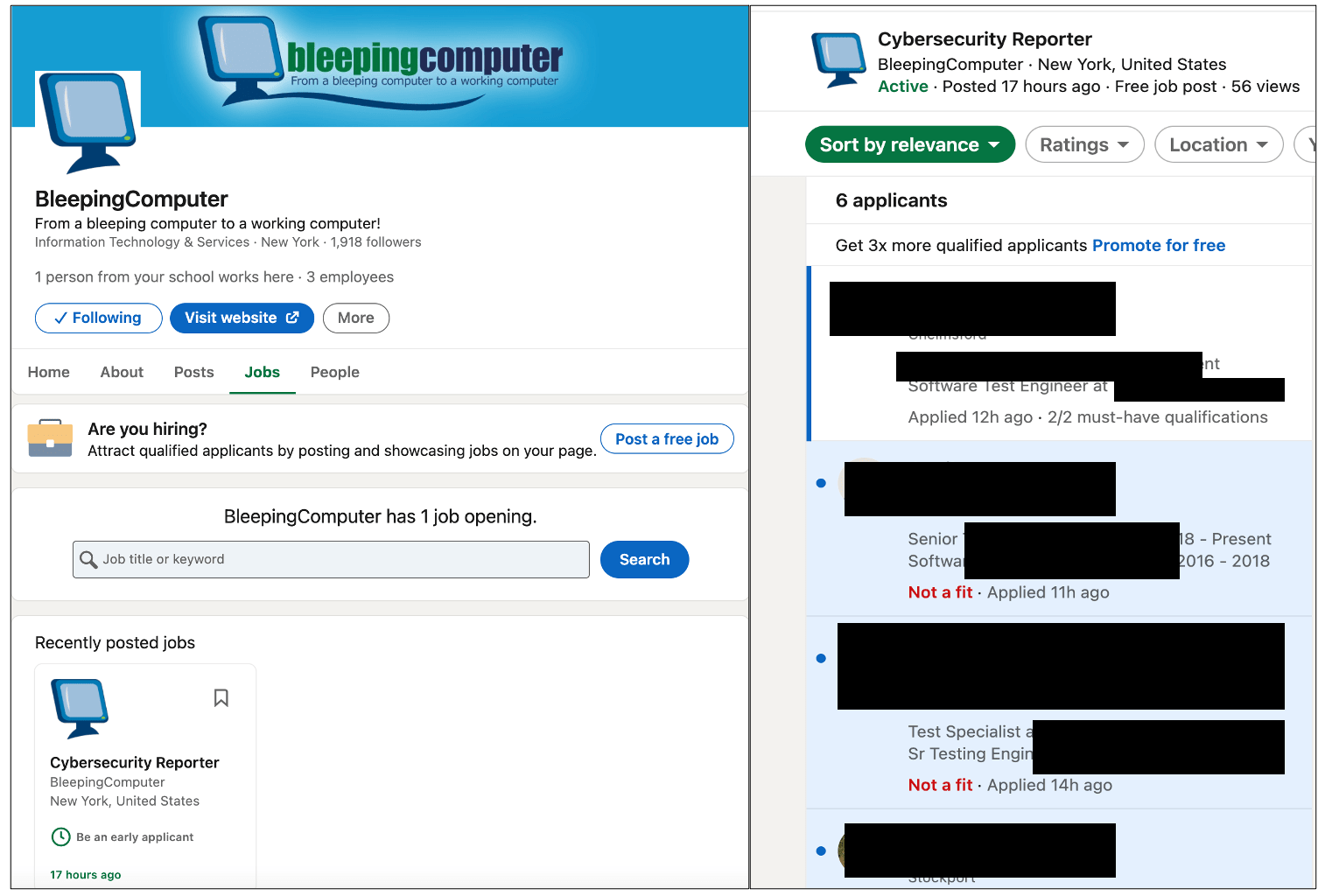
In a brief test, BleepingComputer also leveraged LinkedIn’s “Easy Apply” option such that any resumes uploaded by an applicant would come straight to a test email account, as opposed to LinkedIn redirecting the applicant to an external website.
The organisation found that using a test email account for collecting applicants’ personal information and resumes would leave no indication of any suspicious activity to the applicant or the employer, unlike when redirecting the applicant to a website that may appear “phishy” right away.
Fraudulent listings and phishing scams
Experts like Singh believe this feature has been abused in the past and could become a hotbed for phishing campaigns in the near future.
The feature can be misused by threat actors to target the public for various kinds of frauds and phishing scams.
LinkedIn scams are not exactly something new, with the ones reported thus far mostly relying on someone creating a fake profile and touting themselves as the “recruiter” of a company.
But this form of loophole allows anyone to create a job listing on behalf of virtually any organization, without even revealing their identity.
Restricting who can post jobs under your company
This begs the question: what can you do as an employer to prevent unauthorised parties and threat actors from creating bogus job listings using your organisation?
LinkedIn has previously released a blog post with tips on spotting and avoiding common job scams, but falls well short of addressing the particular issues we mention here.
BleepingComputer confirmed that you cannot take down a bogus job posting yourself, even as the super-admin of your company’s page!
Fortunately, there may be some steps that businesses can take to deter unauthorised job postings.
By default, there isn’t a way for the administrator of a LinkedIn company page to restrict job listings from anyone, but emailing LinkedIn’s safety team seems to do that job:
“You can manually email to the LinkedIn trust and safety team to get those options enabled that allow you to block unauthorised posts, and only allow authorised team members to post jobs,” Singh told BleepingComputer, while sharing the team’s email address: [email protected]
However, as this email address is not shared online by LinkedIn, unless you knew of its existence and the ability to block this “feature,” you are vulnerable to this type of attack.
Additionally, Singh suggests informing your recruitment and HR teams to periodically monitor your company’s LinkedIn pages and report any bogus postings to LinkedIn as a workaround, albeit a slower one.
Contrary to claims by LinkedIn that its AI-based systems can detect fake postings, their automated systems did not detect the tests conducted by BleepingComputer, and the listings were not removed until after the website’s emails to LinkedIn.
Until there is a more permanent solution, LinkedIn users and employers should report suspicious job listings as spam or scam for review by LinkedIn.
But it remains no less than astounding that the world’s premier professional network has not yet implemented best-practice methods to ensuring job-related scams do not take place.




