New FluBot and TeaBot malware distribution campaigns have been detected in Australia, Germany, Poland, Spain, and Romania, using typical smishing lures or laced apps against Android users.
FluBot’s Reappearance:
Fake SMS messages, “Is that you in this video?” coaxing, fake browser updates, and fake voicemail notifications are among the SMS subject lines used to spread FluBot virus.
Bitdefender Labs researchers observed the most current FluBot campaign, intercepting over 100,000 infected SMS messages since December 2021.
FluBot operators, according to the research, launch attacks in short-term waves using different decoys for each country.
After infecting a device, the virus exploits the victim’s contact list to distribute more SMS decoys, obtaining higher infection rates due to receivers’ trust in known contacts and continuing to spread.
The FluBot distribution has been active throughout 2021, and reports of high-volume activity in 2022 show that its operators won’t be slowing down anytime soon.
TeaBot Thriving in the Google Play Store:
TeaBot is a global Android banking Trojan that was identified in January 2021 and has since made many appearances in the Play Store.
It is transmitted to unsuspecting victims using Trojan programmes available on the Google Play Store, such as:
- QR Code Reader – Scanner app – 100,000 downloads
- QR Scanner APK – 10,000 Downloads
- QR code scan – 10,000 downloads
- Smart Cleaner – 1,000 downloads
- Weather Cast – 10,000 downloads
- Daily Weather – 10,000 downloads
At first glance, none of these apps had any malicious code and functioned as promised, allowing them to pass the Google Play Store review process and reach a larger pool of victims.
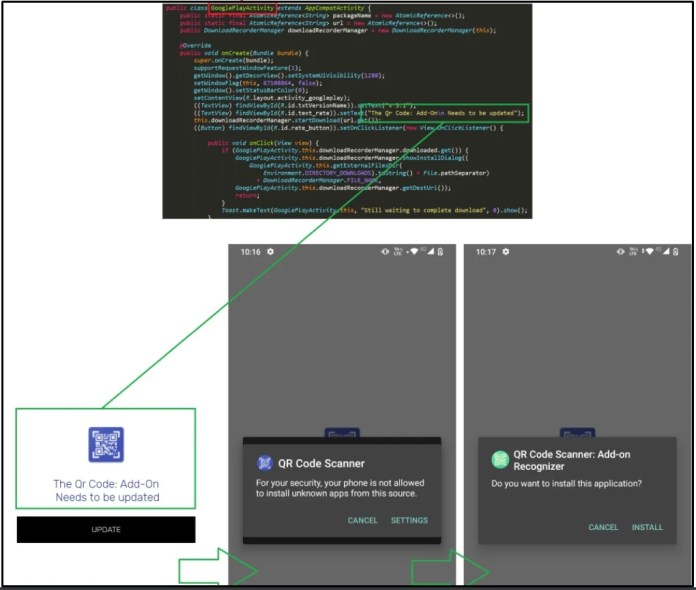
However, once installed and running on the victim’s device, the apps launched a background service that checked the country code and stopped if it returned Ukraine, Uzbekistan, Uruguay, or the United States.
The app downloaded its setup for all other victims, as well as an APK from a GitHub repository containing a TeaBot variation. Simultaneously, apps prompted the user to authorise third-party sources to install packages.
The TeaBot campaign shows clearly that even if you instal software from the Google Play Store, you are not always safe from cybercriminals.
As a result, it is recommended to be cautious with new installs, read user reviews, monitor the app’s network and battery usage, and provide only risk-free permissions.




