Spear phishing campaign targeting Facebook business accounts
The latest phishing scam known as Ducktail targets LinkedIn social media professionals with administrative social media credentials to gain control of Facebook business accounts that manage advertising for victim firms.
The malware primarily targets LinkedIn users who have roles in digital marketing, social media marketing, digital advertising, or similar fields. As a result of Ducktail’s attacks, cookies, IP addresses, account information, two-factor authentication codes, and sensitive corporate data were stolen.
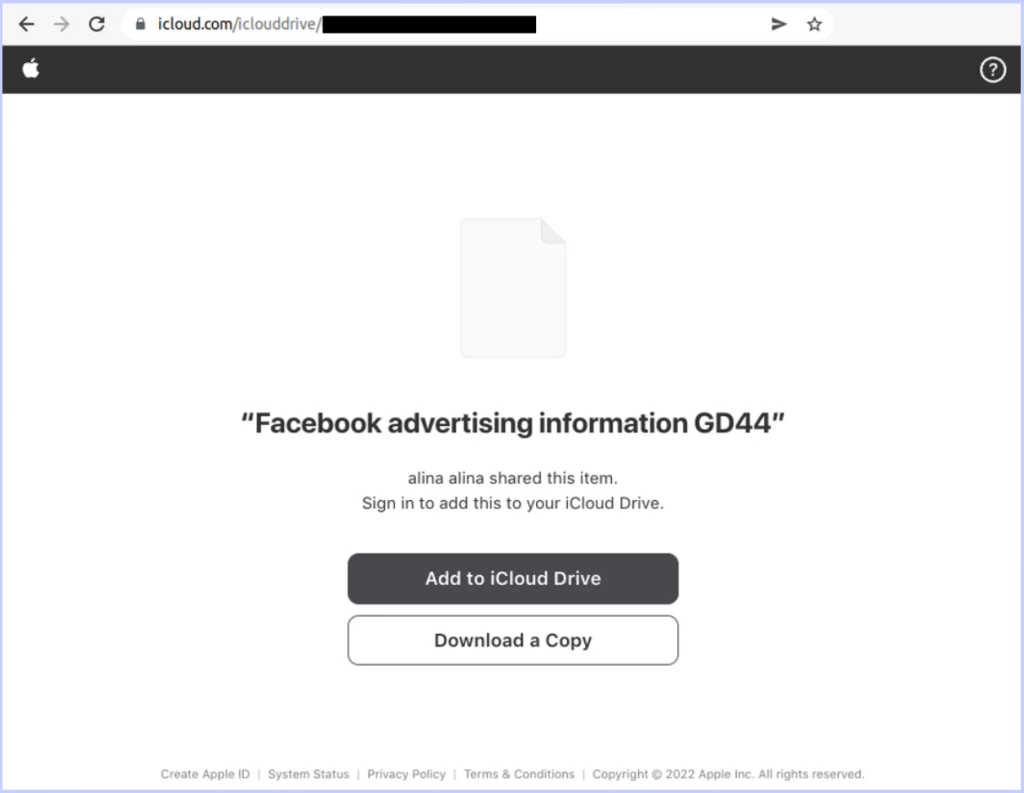
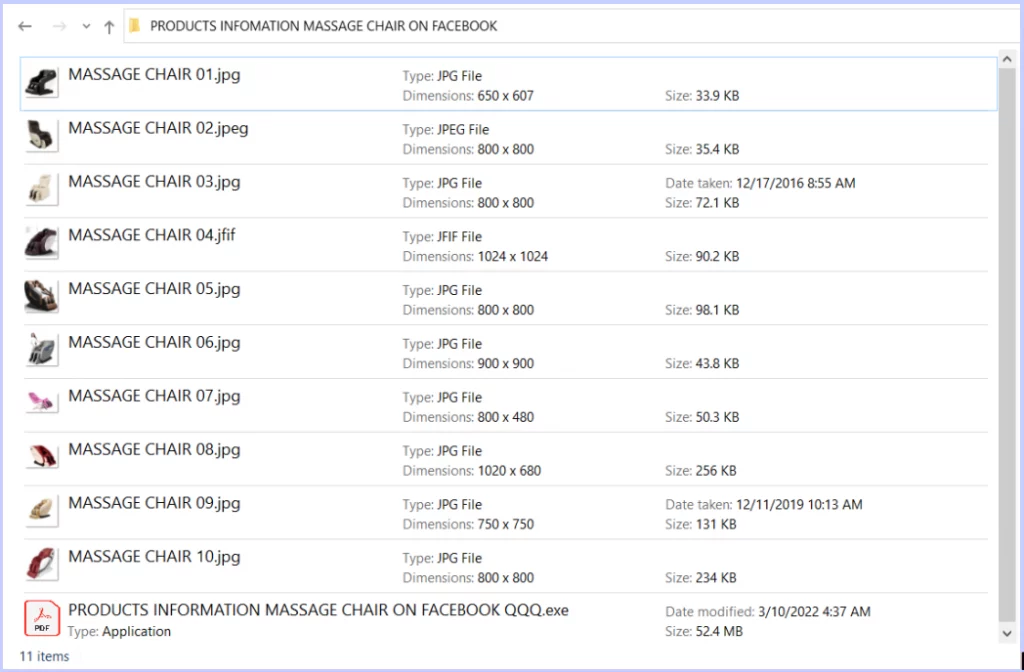
What information was exploited from victims?
Cookies, IP addresses, account information (name, email, birthday, user ID), two-factor authentication (2FA) codes, and geolocation data were stolen. Business-specific details stolen from the compromised accounts include verification status, advertising limits, user lists, client lists, IDs, currencies, payment cycles, payment amounts, and adtrust DSLs (dynamic spending limits).
Along with stealing victims’ personal information, Ducktail hijacks their Facebook accounts by adding a new email address and permissions to the compromised accounts. Using their new privileges, threat actors redirect advertising payments to their own accounts or fund malicious Facebook Ad campaigns from the budgets of victimized firms.
Why spear phishing attacks work
Spear phishing is a targeted email attack that impersonates a trusted sender. With spear phishing, human error is exploited through social engineering techniques, making it hard to defend it exclusively with technology.
As the name suggests, spear phishing implies aiming to catch a specific fish. Emails contain specific material designed to influence recipients to take the actions that the attacker desires. Typically, this includes disclosing their name, personal information, and corporate information.
Signs of spear phishing
- Unfamiliar tone of voice or greeting
- Errors in grammar and spelling
- Email addresses, links, and domain names are inconsistent
- A sense of urgency or threats
- Attachments that seem suspicious (such as .zip, .exe, .scr, etc.)
- The conversation was not initiated by the recipient
- A request for credentials, payment information, or other personal information
How to prevent exploitation from spear phishing
A quality cyber awareness training program is crucial to protect a network against ransomware, phishing, and other social engineering attacks. Phishing attacks are constantly being perpetrated on employees, who must be able to spot red flags when receiving suspicious emails. For staff, training will ensure that critical business information is protected, and senior management will have a clearer understanding of their regulatory requirements for developing effective processes and procedures.




