Threat experts have discovered a new campaign known as ‘OiVaVoii,’ which targets company executives and general managers with malicious OAuth apps and unique phishing lures issued from compromised Office 365 accounts.
According to Proofpoint, the campaign is still running, though Microsoft is keeping an eye on it and has already stopped most of the apps.
The consequences of executive account takeovers range from lateral network movement and insider phishing to the deployment of ransomware and business email exploits.
Employing OAuth Apps
The OiVaVoii campaign’s actors used at least five malicious OAuth applications, four of which are currently blocked: ‘Upgrade,’ ‘Document,’ ‘Shared,’ and ‘UserInfo.’
Three of these apps were created by verified publishers, indicating that the threat actors gained access to a legitimate Office tenant’s account.
After that, the threat actors used the apps to send authorisation requests to high-ranking officials in the targeted firms.
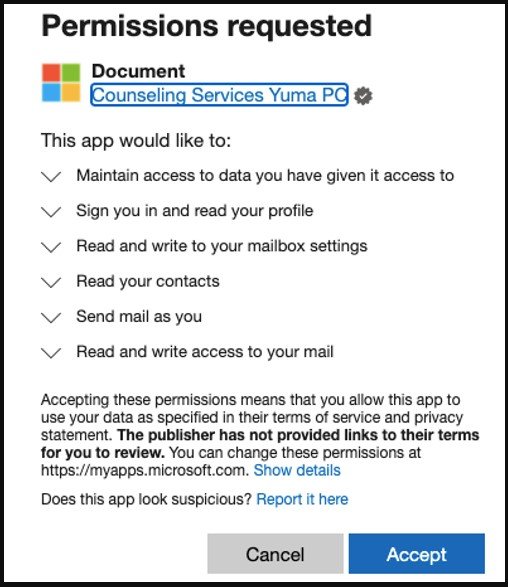
When victims click Accept, the threat actors utilise the token to send emails from their accounts to other employees inside the same firm.
Proofpoint also warns of the possibility of man-in-the-middle proxy attacks, which could compromise the target’s account credentials.
Campaign Is Still Active
Four of the malicious OAuth apps used by the actors in this campaign have been blocked, but new ones are being created and employed in the same way. Executives who have already been compromised and given access to their accounts are still high-risk points for impacted organisations.
The potentially compromised firms need to revoke the permissions, delete the apps, remove any malicious mailbox rules added by the actors, and scan for any dropped files.
Finally, all employees should be trained to be sceptical of official emails, especially messages from high-ranking executives that don’t align with their standard business practices.




